Edge AI: The Native Path to CRA Compliance
Solve 5 out of 13 Cyber Resilience Act requirements automatically by design. Keep data local, minimize attack surfaces, and ensure resilience with On-Device AI.
Why Edge AI is the Strategic Choice for Compliance
The Cyber Resilience Act (CRA) demands strict data minimization, confidentiality, and resilience. Traditional cloud-first AI architectures struggle here: they transmit massive amounts of raw data, creating large attack surfaces and privacy risks.
Edge AI flips this model. By processing data directly on the device using TinyML, raw sensor data never leaves the hardware. Only actionable insights are transmitted. This architectural shift doesn't just improve performance—it makes compliance a built-in feature rather than an afterthought.
In the case of data relevant under the GDPR (General Data Protection Regulation), this must of course be considered in every instance.
(Note: "DSGVO" is likely a typo for DSGVO, the German abbreviation for Datenschutz-Grundverordnung, which is the GDPR in English.)
From Raw Data to Instant Insight
Our Edge AI architecture processes sensor streams locally, fundamentally changing the data lifecycle.
Data Capture: High-bandwidth sensors (cameras, microphones, vibration sensors) capture raw data streams locally on the device.
On-Device Inference: A specialized TinyML chip analyzes the data in real-time using optimized neural networks. No data is sent to the cloud for processing.
Insight Extraction: The device extracts only the specific event or state (e.g., "Anomaly Detected", "Person Identified").
Secure Transmission: Only this lightweight metadata (bytes instead of megabytes) is encrypted and sent to the cloud.
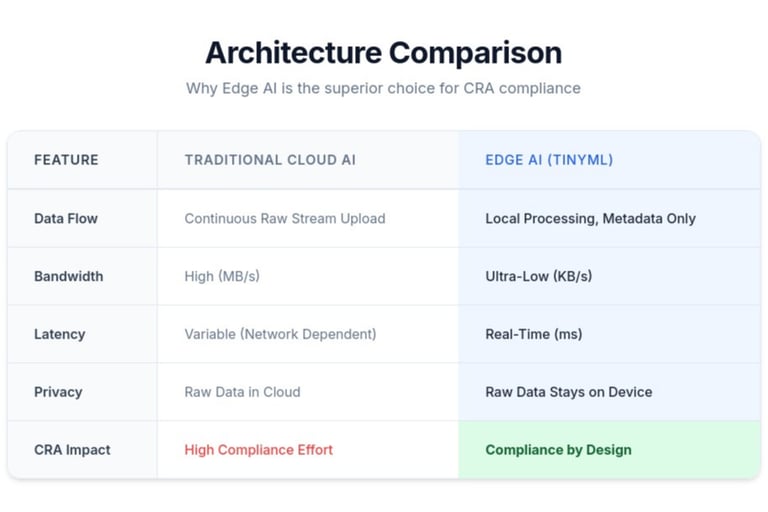
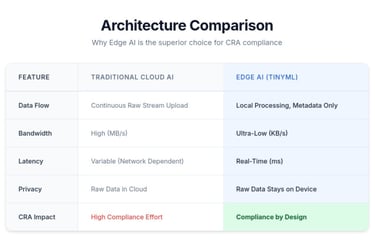

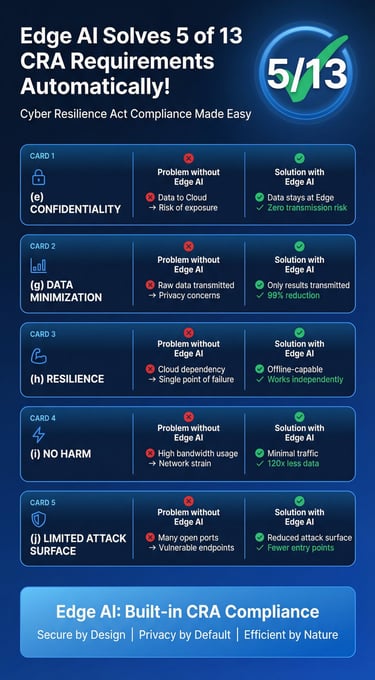
By deploying Edge AI, you address nearly 40% of the CRA's essential requirements through architectural design alone.
1. (e) Confidentiality of Data
The Challenge: Protecting sensitive data from unauthorized access during transmission and storage.
The Edge AI Solution: Raw data (video, audio, biometrics) never leaves the physical device. It is processed in volatile memory and discarded immediately. There is no "data in transit" to intercept.
2. (g) Data Minimization
The Challenge: Collecting only data strictly necessary for the function.
The Edge AI Solution: Instead of storing 24/7 video feeds, the system only records and transmits the specific event of interest. Data volume is reduced by up to 99%, perfectly aligning with the principle of minimization.
3. (h) Resilience and Availability
The Challenge: Ensuring functions remain available during network outages or attacks.
The Edge AI Solution: Edge devices operate autonomously. Even if the network is cut or the cloud is unreachable, the AI continues to detect and act locally, ensuring critical functionality is never lost.
4. (i) No Harm to Connected Systems
The Challenge: Preventing devices from endangering the network (e.g., via DDoS participation).
The Edge AI Solution: By transmitting only tiny packets of metadata, Edge AI devices consume minimal bandwidth. They cannot be easily weaponized to flood networks with high-volume traffic.
5. (j) Limited Attack Surface
The Challenge: Reducing the number of entry points for attackers.
The Edge AI Solution: Edge AI devices do not need open listening ports for incoming cloud commands or massive data pipes. They can operate in a "push-only" mode, significantly reducing the digital footprint exposed to the internet.
Use Cases
Privacy-First Smart Home
Scenario: A security camera detects intruders without streaming private living room footage to a cloud server.
CRA Benefit: Maximizes Confidentiality and Data Minimization.
Industrial Predictive Maintenance
Scenario: A vibration sensor on a critical pump analyzes health locally and only alerts when failure is imminent.
CRA Benefit: Ensures Resilience—monitoring continues even if the factory network goes down.
Voice Control for Medical Devices
Scenario: A surgical robot responds to voice commands processed locally, ensuring zero latency and zero recording of patient conversations.
CRA Benefit: Critical Availability and patient Data Privacy.





Built on Proven Standards
Hardware: ESP32-S3, ARM Cortex-M, RISC-V Accelerators
Frameworks: TensorFlow Lite for Microcontrollers, Edge Impulse
Connectivity: MQTT over TLS 1.3 (Secure, Lightweight)
Security: Hardware Root of Trust, Secure Boot, Flash Encryption