CRA Compliance
The definitive guide to the EU Cyber Resilience Act. Understand the 13 requirements, timeline, and your path to conformity.
Explore Requirements
Section description: Annex I of the CRA outlines mandatory cybersecurity requirements for all products with digital elements.
Requirements:
No Known Exploitable Vulnerabilities
description: Products must not be released with known exploitable vulnerabilities. Manufacturers must have a vulnerability management process in place before release.
Action: Implement SAST/DAST & Dependency Scanning
Secure by Default Configuration
description: Devices must ship with secure settings. Unnecessary services disabled, no weak default passwords, and a secure reset mechanism.
Action: Harden default configs & remove default passwords
Security Updates and Opt-out
description: Automatic security updates enabled by default with a clear opt-out mechanism. Users must be notified of updates.
Action: Build OTA update infrastructure
Protection Against Unauthorized Access
description: Implement strong authentication (MFA, RBAC) and identity management to prevent unauthorized access.
Action: Enforce MFA & Role-Based Access
Confidentiality of Data
description: Protect sensitive data at rest and in transit using state-of-the-art encryption (e.g., AES-256, TLS).
Action: Encrypt all sensitive data flows
Integrity of Data and Functions
description: Protect against unauthorized manipulation of data and system functions. Use secure boot and signed firmware.
Action: Implement Secure Boot & Code Signing
Data Minimization
description: Collect only data strictly necessary for the product's function. No excessive data processing.
Action: Audit data collection practices
Resilience and Availability
description: Ensure basic functions remain available during security incidents (e.g., DoS attacks).
Action: Implement DoS protection & failover
No Harm to Connected Systems
description: Products must not endanger other devices or networks (e.g., by generating excessive traffic).
Action: Rate limit network traffic
Limited Attack Surface
description: Minimize exposure by closing unused ports and reducing system complexity.
Action: Close unused ports & services
Mitigation of Incident Impact
description: Use technical measures like sandboxing and memory protection to limit the blast radius of an attack.
Action: Implement sandboxing & isolation
Logging of Security-Relevant Activity
description: Record security events (access, changes) and allow users to view or disable logging.
Action: Centralized security logging
Secure Deletion and Data Portability
description: Allow users to permanently delete personal data and securely transfer it to other systems.
Action: Add 'Delete All Data' feature
Conformity Assessment
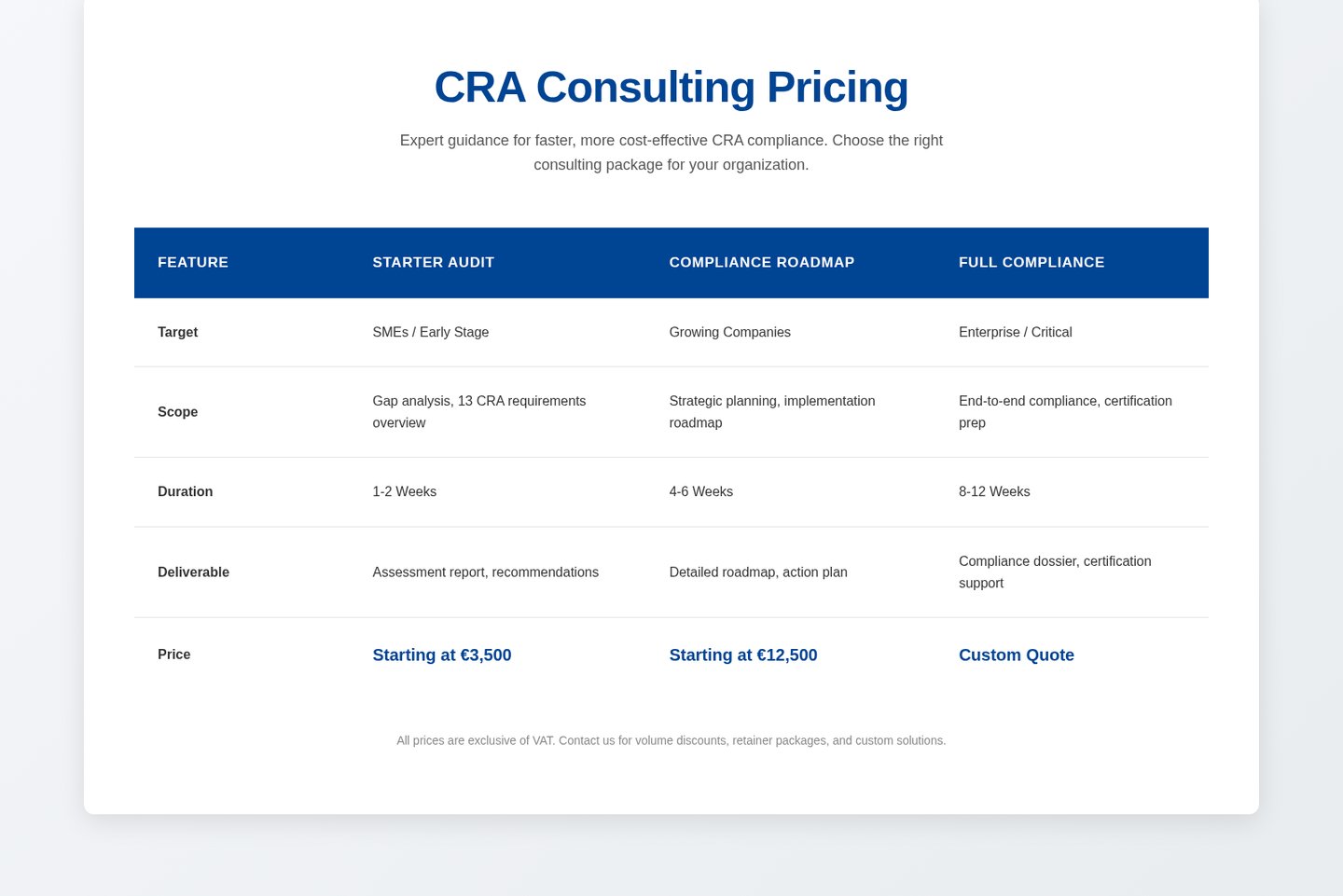
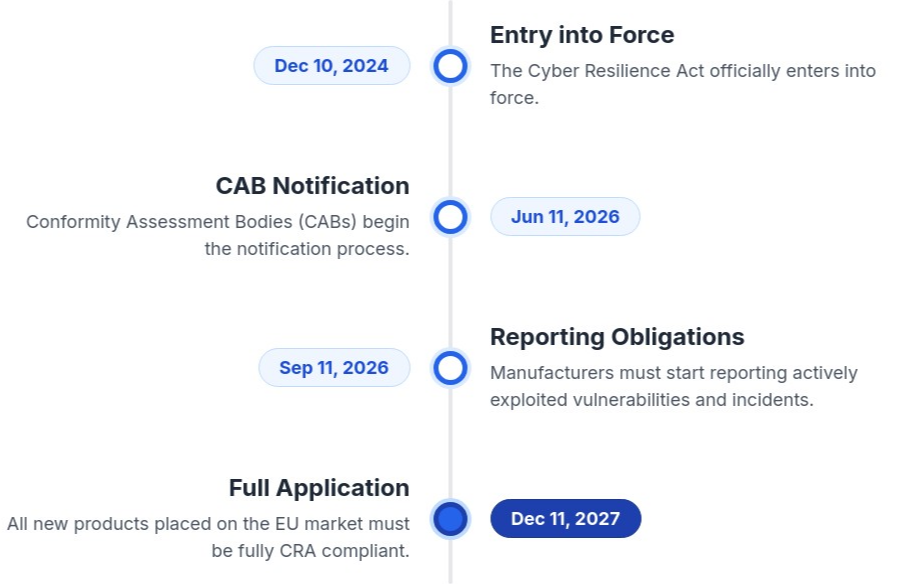
View Timeline - Key dates you need to know
Not all products are treated equally. The CRA applies a risk-based approach to conformity assessment. Most products (~90%) will fall into the Default category, allowing for self-assessment.
Steps:
Determine Category: Classify your product as Default, Important (Class I/II), or Critical based on Annex III/IV.
Risk Assessment: Perform and document a cybersecurity risk assessment specific to your product.
Implement Requirements: Address all 13 essential requirements and vulnerability handling obligations.
Technical Documentation: Compile technical files proving conformity (design, testing, risk analysis)
Conformity Assessment: Perform Self-Assessment (Default) or engage a Notified Body (Critical/Important).
CE Marking: Affix the CE mark and issue the EU Declaration of Conformity.
Q: What products are covered by the CRA?
A: The CRA covers 'products with digital elements' (PDEs). This includes hardware and software connected to a device or network. Examples range from smart home devices and toys to firewalls and operating systems. Exceptions include products already covered by specific regulations like medical devices, aviation, and cars.
Q: What is the difference between Default, Important, and Critical products?
A: Most products fall into the Default category and can be self-assessed. Important products (Class I & II) like routers or OSs may require notified body involvement if harmonized standards aren't used. Critical products (e.g., smart cards, hardware security modules) always require third-party assessment.
Q: What happens if I don't comply?
A: Non-compliance can lead to fines of up to €15 million or 2.5% of global turnover, whichever is higher. Additionally, market surveillance authorities can order the withdrawal or recall of non-compliant products from the EU market.
Q: Do I need to certify my existing products?
A: The CRA applies to products placed on the market after the enforcement date (Dec 2027). However, if you make 'substantial modifications' to an existing product, it may be treated as a new product and require compliance. Security updates alone typically do not trigger this.
Q: How does CRA relate to GDPR?
A: While GDPR focuses on personal data privacy, CRA focuses on the cybersecurity of the product itself. They are complementary. CRA requirements like 'Confidentiality of Data' and 'Secure Deletion' directly support GDPR compliance.